Up next
2.23.24: Cyber Attacks? Lies, Ghost, Children and Borders, Illegals, Phase 2, Pray!
Deep State Criminals Panic ReeEEeE Stream 06-09-24
Doom Threepeater vs 99 Giga Gargantuar vs Dr Zomboss - Plants vs Zombies Hack
GLOBAL ACCOUNTS OF MEDIEVAL UFO/UAP BATTLES IN OUR SKIES!
Jon Zherka 24 Hour Sleep Stream.. DAY 2
Cyber attacks stall business at car dealerships nationwide
Biden's Open Border is a Refuge For Criminals
Joe Biden has more respect for literal criminals than his own citizens
How Summer let go of trying to control her sleep and regained control over her life (#58)
GAIN OF FUNCTION CRIMINALS ARE SQUIRMING
Criminals at The Border or News Propaganda? Texas at War with Biden? | Shawn Bolz
Puffy Royal Mattress Unboxing #shorts #sleep #mattress
How to Manage Multi-Social Accounts For Marketing
Working for One of the Most Notorious Criminals #shorts
PCAST: Discussion of reports: Cyber-physical Resilience; Reduction of Greenhouse Gas Emissions
Real-Life Accounts From Those Who Witnessed John Lennon's Murder
Putting Patients First: The Case for Individual Health Accounts
No sleep till Iowa | FiveThirtyEight Politics Podcast
SEA SERPENTS Eyewitness Accounts PART III
Guided Meditation for Going Consciously Into the Sleep Cycle (with Lilla)
Are The Gospels Accurate Eye-Witness Accounts? | Dr. Robyn Faith Walsh
PROPHET OF DOOM Predicts Cyber Attacks, Flooding and Mass Chaos In 2024
SEA SERPENTS Eyewitness Accounts PART II
What to know about the travel "hack" called #skiplagging and why it's risky #travelhack #travel #fly
Which countries get the best night's sleep?
Holiday party hacks #christmas #party #hack
A Modern History of SEA SERPENTS: Eyewitness Accounts
Crime in SA | Criminals hard at work this holiday season
Obama Predicts CYBER ATTACK, Alex Jones Returns, and the Church of Fauci | PBD Podcast | Ep. 338
Hackers didn't add Amazon locker addresses to accounts #shorts #amazon #shopping #hacker #scam
Timcast IRL - ALEX JONES RETURNS, Elon Musk Restores Jones, Rumble Hit By CYBER ATTACK w/Anna Perez
Republicans Can't Hold Their Criminals Accountable While Ignoring Donald Trump!!!
How Opioids Disrupt Quality of Sleep | Dr. Gina Poe & Dr. Andrew Huberman
The Sun's Defence Editor Jerome Starkey analyses Russia's cyber attacks on Britain
ATF Redefining Words to Turn Law-Abiding Gun Owners Into Criminals
Cyber Siege: Unmasking China's Assault on Global Networks
What to know about Google deleting unused accounts #shorts #google #googleaccount #gmail #youtube
Struggling with REM Sleep? Castor Oil and Other Surprising Solutions! | Trailer | Vital Signs
Can We Hack Photosynthesis to Feed the World? | Steve Long | TED
Freed Palestinians share accounts of challenging conditions in Israeli prisons
Nikki Haley Says If Elected, NO MORE ANONYMOUS ACCOUNTS, Will Mandate Internet Verification
What Would Happen if You Only Got 5 Hours of Sleep Per Night - NOT GOOD!
Why Alcohol Is Bad Prior to Sleep | Dr. Gina Poe & Dr. Andrew Huberman
Here’s how cyber criminals try to hack your accounts while you sleep
Have you ever felt frustrated by the flood of notifications from your multi-factor authentication (MFA) app? Well, cyber criminals have too. And they’re taking advantage of “MFA fatigue” to try to gain access to your sensitive business data. MFA is essential for keeping your data secure. It adds an extra layer of security to your apps and accounts by asking you to verify your identity in two or more ways, such as a password and a code sent to your phone. The constant alerts can be overwhelming though. Attackers know this and will bombard employees – sometimes in the middle of the night – with a constant stream of MFA notifications. Which makes it more likely someone will authenticate a login attempt through frustration, tiredness, or just to get the notifications to stop. But now there’s a new weapon in the fight against MFA fatigue. Microsoft Authenticator has introduced number matching as a way of making sure your MFA notification is from the correct login attempt, preventing cyber criminals from taking advantage of notification fatigue. How does number matching work? When you receive an MFA notification, the app will display a randomly generated number. You then need to input this number to authenticate the login attempt and prove you’re not a cyber criminal trying to access your business data. That’s not all. Microsoft Authenticator also allows for biometric authentication, which means you can use your face, fingerprint, or other unique physical features to prove your identity and combat the threat of MFA fatigue attacks. With these security measures in place, your business can stay ahead of cyber criminals and keep your sensitive data better protected. If you already use Microsoft Authenticator, number matching is ready to use. Simply make sure your app is up-to-date, and you’ll be protected. If you use another MFA system and want to look at how to make your security better or easier, we can help. Get in touch. Published with permission from Your Tech Updates.
- Top Comments
- Latest comments

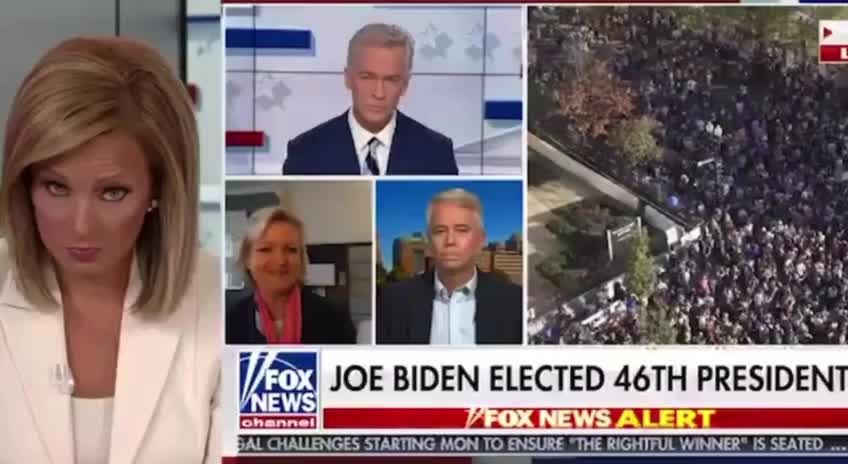










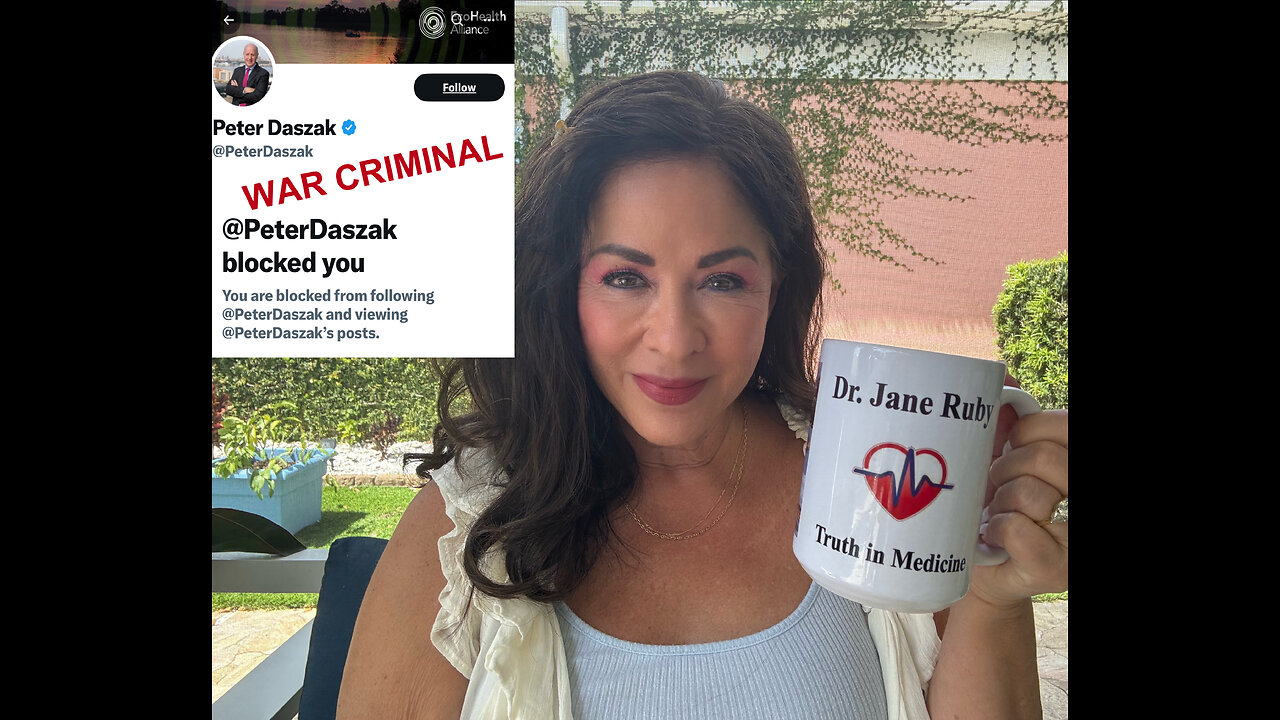
















![Ep 3118b - [DS] Change Of Batter, Charlie Monitors & Protects Election, Cyber Attack Attempts](https://ak2.rmbl.ws/s8/1/-/P/7/3/-P73k.qR4e-small-Ep-3118b-DS-Change-Of-Batte.jpg)



















